The Privacy Imperative: Building Freedom Through Technology
"Privacy is an important guarantor of decentralization: whoever has the information has the power." Vitalik Buterin's statement cuts to the heart of crypto's founding promise. Zero-knowledge proofs revolutionized blockchain privacy—they can "protect our identities while revealing enough information to prove that we are trustworthy." But there's a critical vulnerability: ZK proofs hide data from the verifier, not from the prover.
Your "private" transactions, trading positions, and sensitive data are completely visible to whoever runs the proving infrastructure.
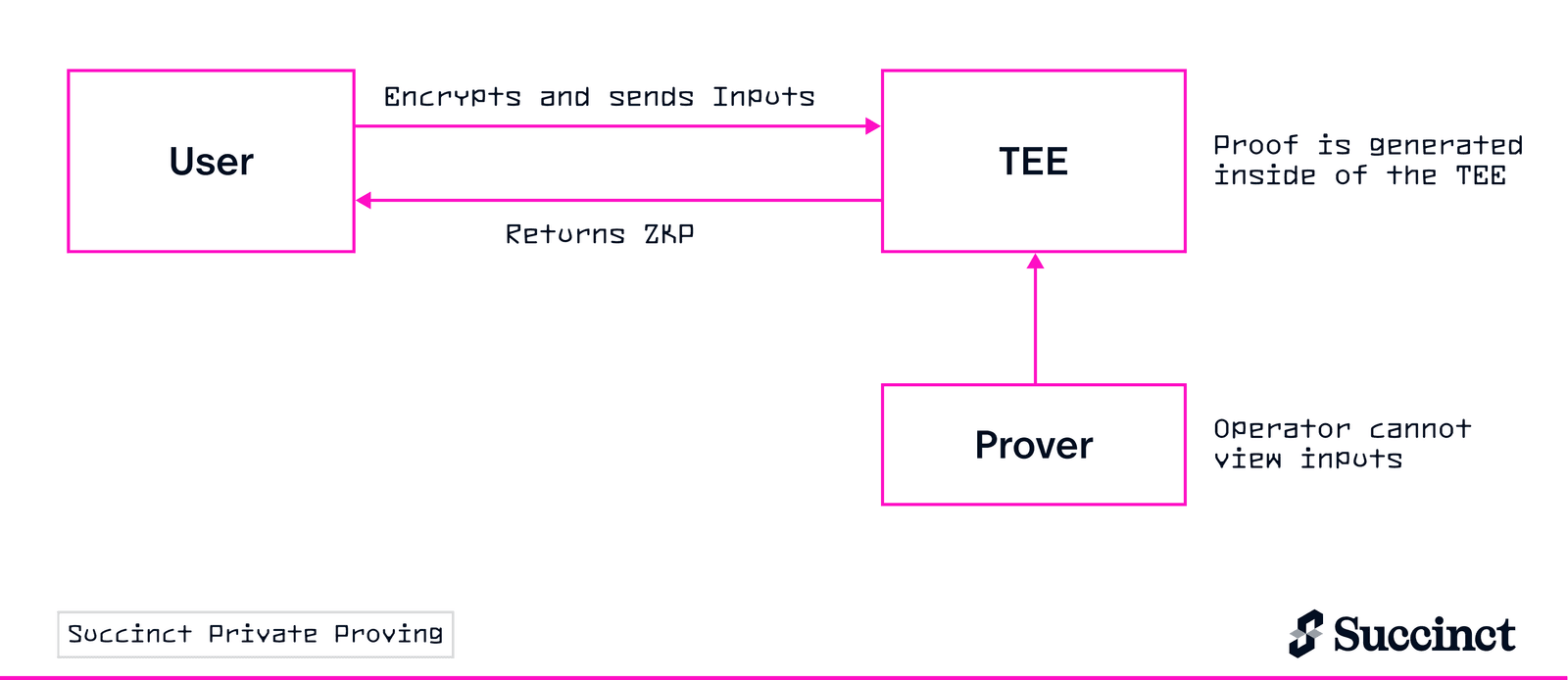
That's changing. Succinct Labs recently launched Private Proving on their Prover Network, powered by Phala Network's TEE infrastructure. For the first time, developers can generate zero-knowledge proofs where neither the verifier nor the prover can see the private inputs. Privacy and verifiability, finally unified.
The Hidden Vulnerability in Traditional ZK
Zero-knowledge proofs are cryptographic marvels. They allow you to prove a computation was performed correctly without revealing the inputs, intermediate steps, or any private data to the verifier. But here's what most people miss: ZK proofs hide data from the verifier, not from the prover.
During proof generation, the witness data—all your private inputs—must be processed by whoever is running the prover. In traditional ZK systems, this means your sensitive information is completely exposed to the prover operator.
The Real-World Implications
Consider what this means for applications claiming to offer privacy:
Private DEXs: You submit a trade to a privacy-preserving decentralized exchange. The ZK proof ensures the verifier can't see your position or strategy. But the prover operator—running the proving infrastructure—sees everything: your wallet address, trade size, entry price, liquidation points, and entire trading strategy. Your "private" trade just revealed your complete position to centralized infrastructure.
Private Payments: You're making a confidential transaction. The proof hides the amount and recipient from the blockchain verifier. But the prover sees the sender, receiver, and exact amount during proof generation. Privacy theater, not privacy reality.
Private Identity Systems: You want to prove creditworthiness without revealing personal data. The ZK proof works—the verifier sees nothing. But the prover operator has access to your credentials, financial history, and all the sensitive data you're trying to protect.
Worse, you can't even verify the prover is protecting your data. There's no cryptographic way to prove that a centralized prover operator isn't logging your witness data, selling it, or getting hacked. You must simply trust them.
The promise of "don't trust, verify" breaks down when you must trust the prover with your most sensitive data—and can't verify that trust.
The Solution: Private Proving with zkVM in TEE
The breakthrough comes from combining two powerful security paradigms: cryptographic verification through zero-knowledge proofs and hardware isolation through Trusted Execution Environments.
This is exactly what Succinct Labs achieved with their Private Proving feature, built on Phala Network's TEE infrastructure. It solves both problems:
- Hardware isolation protects witness data from prover operators at the silicon level
- Remote attestation proves the prover is in TEE, so users can verify—not just trust—that their data is protected
It's not just an incremental improvement—it's a fundamental shift from "trust the prover" to "verify the prover" in zero-knowledge systems.
How Succinct Implemented Private Proving with Phala
Succinct’s Private Proving feature is built on top of the SP1 zkVM, their zero-knowledge virtual machine. To bring hardware-level privacy to proving, Succinct deployed Private Proving on Phala Cloud’s TEE infrastructure, where SP1 zkVM runs securely inside confidential virtual machines.
Phala's Infrastructure:
- Phala Cloud: TEE-enabled compute infrastructure with NVIDIA H200 GPUs
- dstack SDK: Open-source framework for deploying confidential containers—run any Docker image in TEE without code modifications
- TEE GPU Support: NVIDIA H200 with Confidential Computing mode + Intel TDX for VM-level isolation
Succinct's Integration:
- SP1 zkVM inside Private Proving: Packaged as a Docker container and executed within Phala Cloud’s TEE environment
- Zero code changes: Succinct’s existing SP1 prover integrated directly with Phala’s trusted hardware
- Click to deploy: Developers use Phala Cloud to launch private proving infrastructure
The beauty of this architecture is its radical simplicity. Succinct didn't rewrite their zkVM or learn TEE programming. They packaged SP1 as Docker, deployed it through Phala Cloud's web interface, and gained hardware-level privacy. The entire proving process happens inside a hardware-isolated environment where witness data is encrypted at the silicon level—infrastructure teams just click to enable it.
The Private Proving Flow
Here's what happens when you generate a private proof:
- Input Submission: Your sensitive witness data is sent directly to the TEE
- Hardware Isolation: Intel TDX creates a hardware-isolated VM where memory is encrypted
- Secure Processing: SP1 zkVM runs inside this secure enclave, processing your private inputs
- Proof Generation: The NVIDIA H200 GPU (running in CC mode) accelerates proving while maintaining encryption
- Public Output: Only the final ZK proof leaves the TEE—witness data never exits the secure enclave
- Attestation: Remote attestation proves the computation ran in a genuine TEE with verified code
The witness data flows from your application into hardware-protected memory, gets processed by the zkVM, and only the cryptographic proof emerges. At no point can the prover operator, cloud provider, or even Phala itself access your private inputs.
This is what Vitalik envisioned: protecting identities while proving trustworthiness, now realized in production infrastructure.
Technical Deep Dive: How It Works
Let's pull back the curtain on the technical architecture that makes private proving possible.
The Hardware Layer
At the foundation sits the NVIDIA H200 NVL GPU, a powerhouse designed for AI and high-performance computing, now applied to zero-knowledge proving:
- Confidential Computing mode: Hardware-level memory encryption protecting data in use
- Intel TDX integration: VM-level isolation ensuring the entire proving environment is hardware-protected
The system runs on dual Intel Xeon Platinum 8558 CPUs (96 cores total) with 2TB of system memory, providing the computational substrate for running TEE-enabled virtual machines at scale.
The Software Stack: dstack Architecture
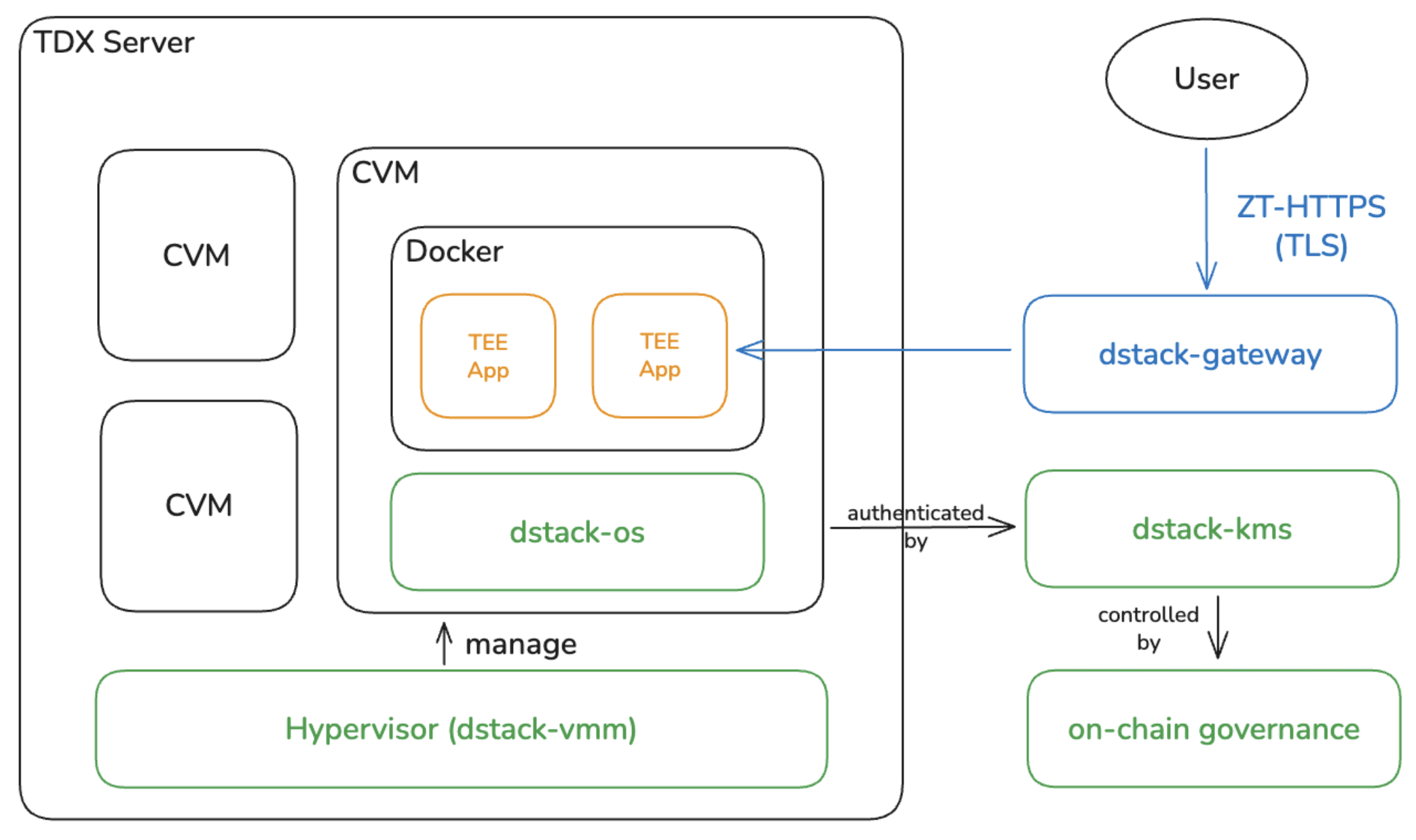
Phala's dstack framework bridges raw TEE hardware and usable infrastructure. This architecture solves critical challenges in making TEE practical for Web3:
- Portable Confidential Containers: Applications aren't locked to specific hardware, addressing vendor lock-in concerns
- Decentralized Code Management: Smart contracts govern application deployment and upgrades, creating an immutable audit trail
- Verifiable Domain Management: Standard browsers can verify TEE applications without client modifications
For Succinct, this meant they could package SP1 zkVM as a standard Docker image and deploy it to Phala's TEE infrastructure without rewriting any core proving logic.
Performance Reality: Benchmarked Overhead
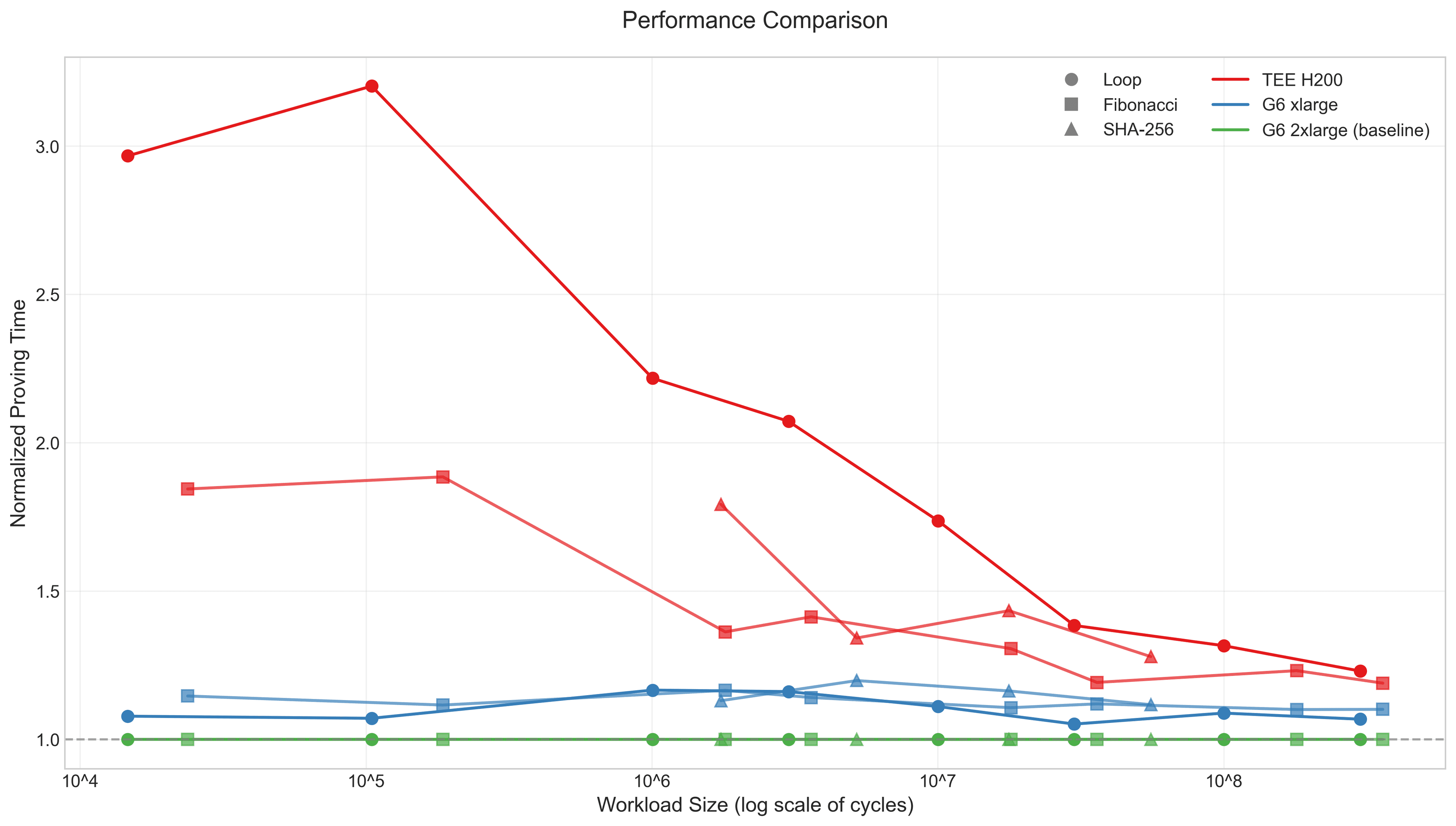
One common concern with TEE is performance overhead. Phala and Succinct collaborated on comprehensive benchmarking to measure the real-world impact, published in their performance benchmark report.
Key findings:
- Sub-20% overhead: For SP1 zkVM workloads, TEE overhead converges to less than 20% as task complexity increases
- Decreasing overhead pattern: The more complex the computation, the lower the relative overhead
- Near-zero for large workloads: In related research on TEE scalability for large-scale LLM inference, Phala demonstrated that for majority of typical queries, overhead remains below 7%, with larger models experiencing nearly zero overhead
The primary overhead comes from memory encryption, but this impact decreases proportionally for longer-running tasks. For zkVM proving—which is computationally intensive and runs for extended periods—the overhead becomes negligible.
Developer Experience: Radically Simple
The remarkable aspect of Phala's approach is how it removes all friction:
For Application Developers:
- Write standard Rust code for SP1 zkVM
- No circuit development, no cryptographic expertise required
- No TEE-specific code changes
For Infrastructure Teams:
- Package your application as a Docker image (you probably already have this)
- Visit Phala Cloud web interface
- Select TEE GPU configuration (H200 available)
- Click deploy
That's it. Your application now runs in a hardware-isolated TEE with:
- Witness data encrypted at silicon level
- Cryptographic proofs of correctness
- Remote attestation of secure execution
- GPU acceleration for high performance
No circuits to write. No specialized TEE knowledge required. No code modifications. Just deploy standard Docker containers through Phala Cloud's interface and get both privacy and verifiability.
This is why Succinct chose Phala—production-ready infrastructure that's as easy to use as traditional cloud, but with hardware-level privacy guarantees.
Use Cases Unlocked
By running SP1 zkVM inside Phala’s secure TEE infrastructure, Private Proving turns theoretical privacy into production reality. The result is a foundation for secure computation across DeFi, identity, and AI — where data remains private, yet proofs remain verifiable:
- Private Stablecoins Prove reserves without revealing individual balances. Verify collateralization without exposing positions. Users get privacy, regulators get verifiability.
- Private Identity Systems Prove creditworthiness without revealing credit history. Verify age without exposing birth date. Show eligibility without sharing credentials. Privacy-preserving KYC for Web3.
- Private DeFi Strategies Execute complex trading strategies without revealing your approach. Provide proofs of fund provenance without exposing transaction history. Build on-chain reputation without doxxing activity.
- Confidential AI Computation A brief but important note: The same TEE GPU infrastructure enabling private proving also powers confidential AI inference. As AI surveillance capabilities grow—a concern Vitalik has highlighted—Phala's infrastructure offers a defense: running AI models where even the infrastructure provider cannot access your queries or model weights. Privacy and verifiability extend beyond ZK to the full spectrum of sensitive computation.
The pattern is consistent: anywhere you need to prove something without revealing everything, private proving delivers.
The Path Forward: Building for Privacy
Vitalik's vision for privacy in crypto is no longer theoretical. The technology exists. The infrastructure is production-ready. The applications are live.
What was once a choice between privacy and verifiability is now a choice to have both. What was once trust in centralized provers is now cryptographic verification of decentralized infrastructure. What was once exposure of witness data is now hardware-encrypted privacy guarantees.
Privacy is no longer optional. In a world of increasing AI surveillance and centralized data collection, the tools we build today determine the freedoms we preserve tomorrow.
Join the Zero-Trust Computing Movement
The future of privacy in crypto is being built now. Whether you're:
- Building the next private rollup
- Creating privacy-preserving DeFi protocols
- Developing confidential identity systems
- Researching new applications of ZK + TEE
The infrastructure is ready. The performance is proven. The applications are in production.
Resources to Get Started:
- Phala Cloud: Deploy confidential applications to TEE
- dstack Whitepaper: Technical deep dive into zero-trust platform architecture
- SP1 zkVM Performance Benchmarks: Real-world overhead measurements
- Succinct Private Proving: Production private proving feature